Tl;dr: Zengo guarantees access to your funds even if you lose your phone and even if Zengo, the company, ceases to operate.
At Zengo, our mission is to provide a superior user experience that enables our users to simply and securely manage their crypto assets without the typical risks associated with private key management and account recovery. These risks include the theft or loss of personal wallet (hardware/software/mobile) private keys, damaging hacks, and/or brutal failures of custodial service such as exchanges.
The Zengo wallet is non-custodial (meaning we do not have any access or control of your funds) and has no seed phrase vulnerability. Using threshold signatures, we’ve replaced the traditional private key with two independently created “mathematical secret shares” that never meet each other. One share is stored on the customer’s mobile device and the other on the Zengo server. Therefore, even if one of the shares gets compromised, the attacker won’t know the other one and your assets will still be safe.
Ever since we announced Zengo, we have been repeatedly asked: What happens if one of the shares is lost? What happens if I lose my phone? What happens if Zengo, the company, becomes unable to operate at all?
Great questions! At Zengo, we’ve invested a lot of resources in solving these problems, which we agree are critical. This blog post describes our solutions.
How Zengo backups work: User side
The share stored on the customer’s device (the “Personal Share”) can get lost. Your phone might get lost, stolen, or broken and if we didn’t have a proper solution then you could potentially lose access to your funds. That is obviously unacceptable – we quickly realized that the personal share can’t exist solely on the customer’s device.
To prevent this issue, we have introduced a backup process that basically stores the decryption key for an encrypted copy of the “Personal Share” on the user’s personal cloud storage: iCloud (iOS), Google (Android) account and/or DropBox. A copy of the encrypted “Personal Share” is then stored on the Zengo server.
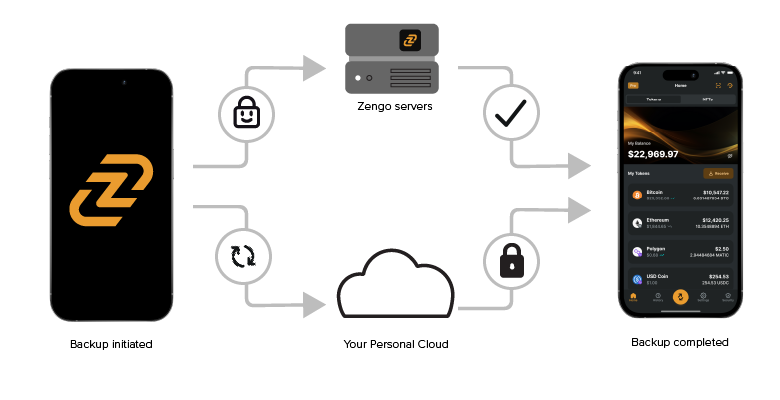
If the Personal Share is lost, users can log in to their personal cloud account (on iOS this happens natively and effortlessly) and access the backup Recovery File (which is the decryption key for the the encrypted Personal Share). Then they use biometric authentication (our 3D FaceLock technology) and other measures to obtain the encrypted Personal share from the Zengo server – which is decrypted on the user’s device and seamlessly allows for account recovery. To learn more about this process, please refer to the security section on the Zengo website.
You can easily verify this process — simply create an account on Zengo, back up your account, deposit a small amount of funds, and delete Zengo from your phone. Install Zengo again, restore your account, and “Voila!”, your account is restored and your funds are accessible again.
How Zengo backups work: Server side
The share stored on the Zengo server (“Remote Share”) is far less susceptible to loss compared to the Personal Share. We use best-in-class cloud-based safeguards and backups to ensure that we never lose the Remote Shares.
However, what happens if the company itself becomes unable to operate? How will transactions ever be signed without the server? Even if we believe the probability of that event to be very low, we had to be prepared for that unlikely scenario. We have invested a substantial amount of time, energy, and resources into addressing this concern.
In response to this scenario, we designed a solution relatively similar in concept to Client Recovery, but without the need for Zengo’s server to be operational. To the best of our knowledge, this is the first such solution in our industry. We call it “CHILL STORAGE™”.
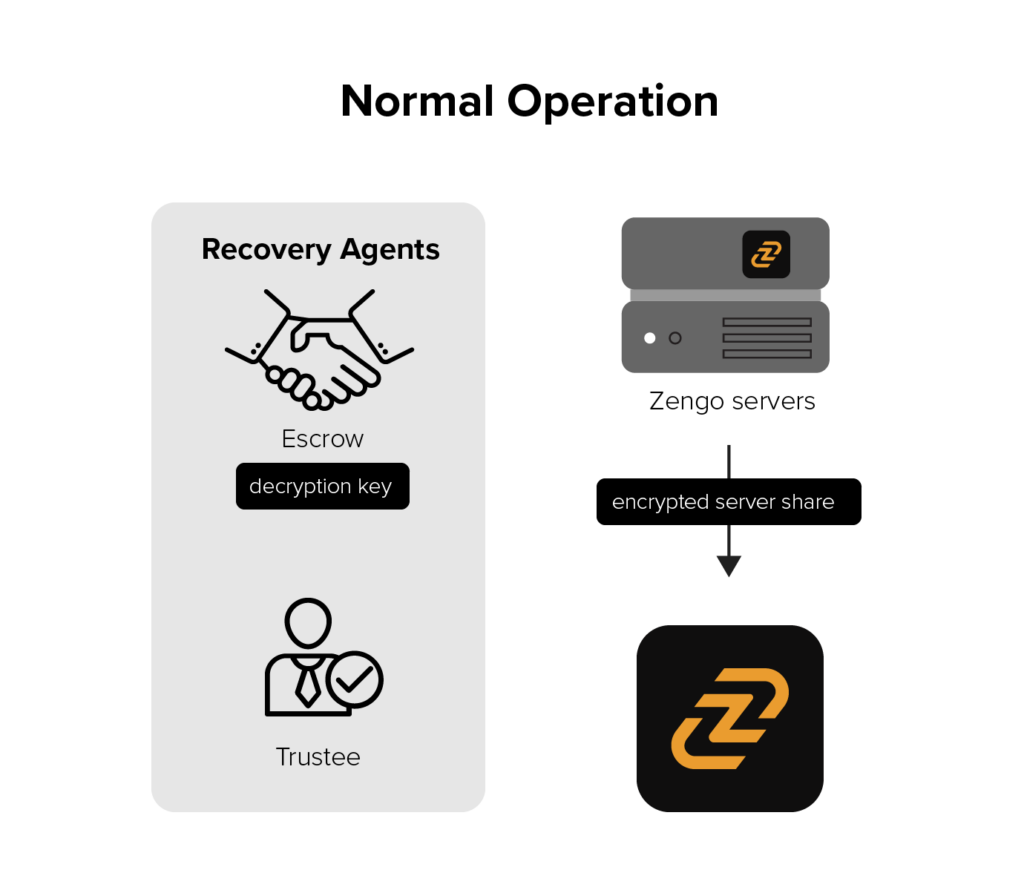
During normal operations:
-
- We instituted this guaranteed recovery process by creating both a master encryption and master decryption key. Next, we deposited this master decryption key in an established escrow (EscrowTech) and appointed a law office (JRG) as trustee. The trustee’s role is to check and report on Zengo “proof of life,” composed of both legal and technical criteria. The master encryption key is maintained on our servers and continuously encrypts the server share, every time a new one is created;
-
- Every client then gets an encrypted version of that remote share (encrypted with the master encryption key);
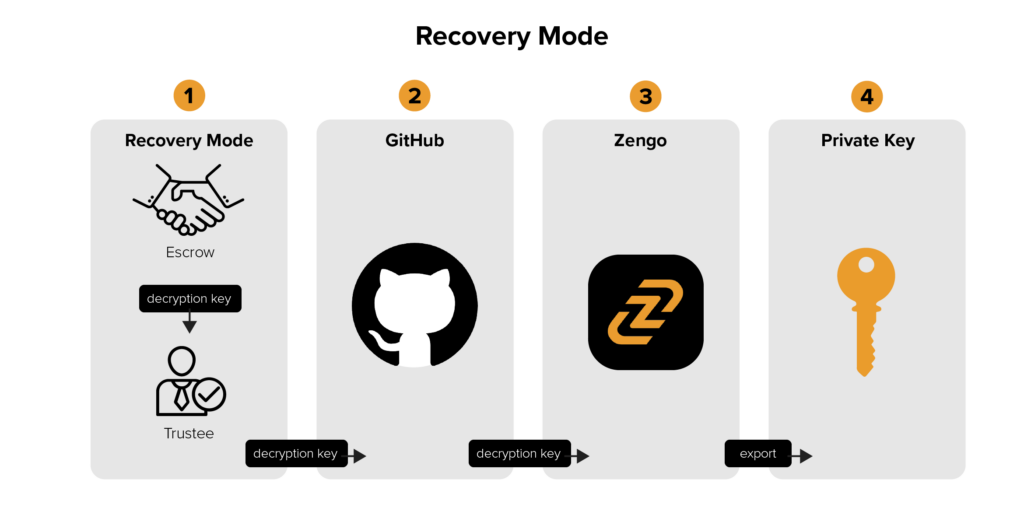
Recovery mode:
-
- If the Trustee discovers that Zengo is not operational, they can request the decryption key from the escrow provider;
-
- The trustee will then post the decryption key to a dedicated GitHub account. This process is run by humans with multiple safeguards and checks to avoid wrong signals;
-
- Zengo, the mobile app installed by our customers, constantly monitors this repository and if a valid key is released, it enters recovery mode;
-
- Upon entering recovery mode, the Zengo app is able to decrypt the encrypted copy of the Remote Share and recreate the private keys for all the associated coins and addresses. These private keys can then be loaded to other wallets. That way, users are free to move their funds without relying upon Zengo servers.
A note on Private Keys computation
As you already know, the Zengo service does not involve typical private keys. Unlike traditional decentralized wallets, Zengo offers its customers a tool to conveniently and securely sign transactions with no private keys — without relying on a custodian.
Zengo uses instead distributed security, by which our servers hold a key share (“Remote Share”) to sign transactions, while the other share is on the user’s mobile device (“Personal Share”). Only when both shares interact can a transaction take place. This means that Zengo is unable to access customers’ assets.
During normal Zengo operations, each share is kept either by the server or client and is never revealed to the other party. However, when both shares are revealed to the same party, it is possible to compute the private key that corresponds to the address controlled by the shares. Using the CHILL STORAGE™ solution, in case Zengo service ceases to operate, the Remote Share that corresponds to the Personal Share is revealed to the customer’s app and the private keys are then computed.
How does that work for Zengo customers?
Before we launched Zengo publicly, we had to test the above solution to guarantee that it works. For that purpose, we simulated the key release with our trustee. Here are the various steps a Zengo customer would go through should the recovery process be triggered by the trustee and escrow company.
-
- Below, you can see a Zengo account with some funds. Note – naturally, you must have an installed working app before the recovery can take place;
-
- The trustee releases the Decryption key to GitHub;
-
- Upon launch, the Zengo app checks the Github URL. If it detects the release of the Decryption key, it activates the “Account Recovery” mode. Now we are able to export the associated private keys from the Zengo wallet to any new wallet;
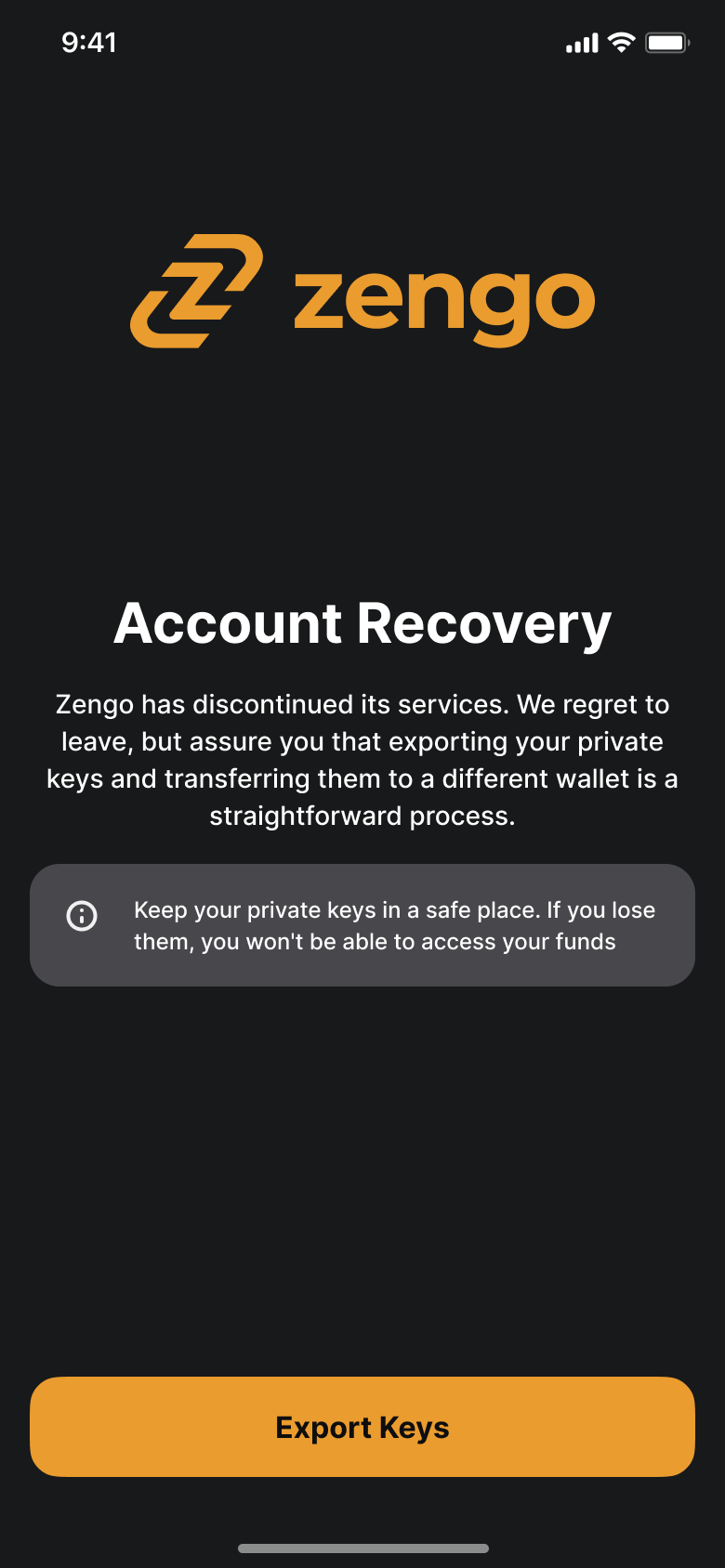
-
- When we clicked “Export Keys,” we were provided with a list of public addresses and their corresponding private key;
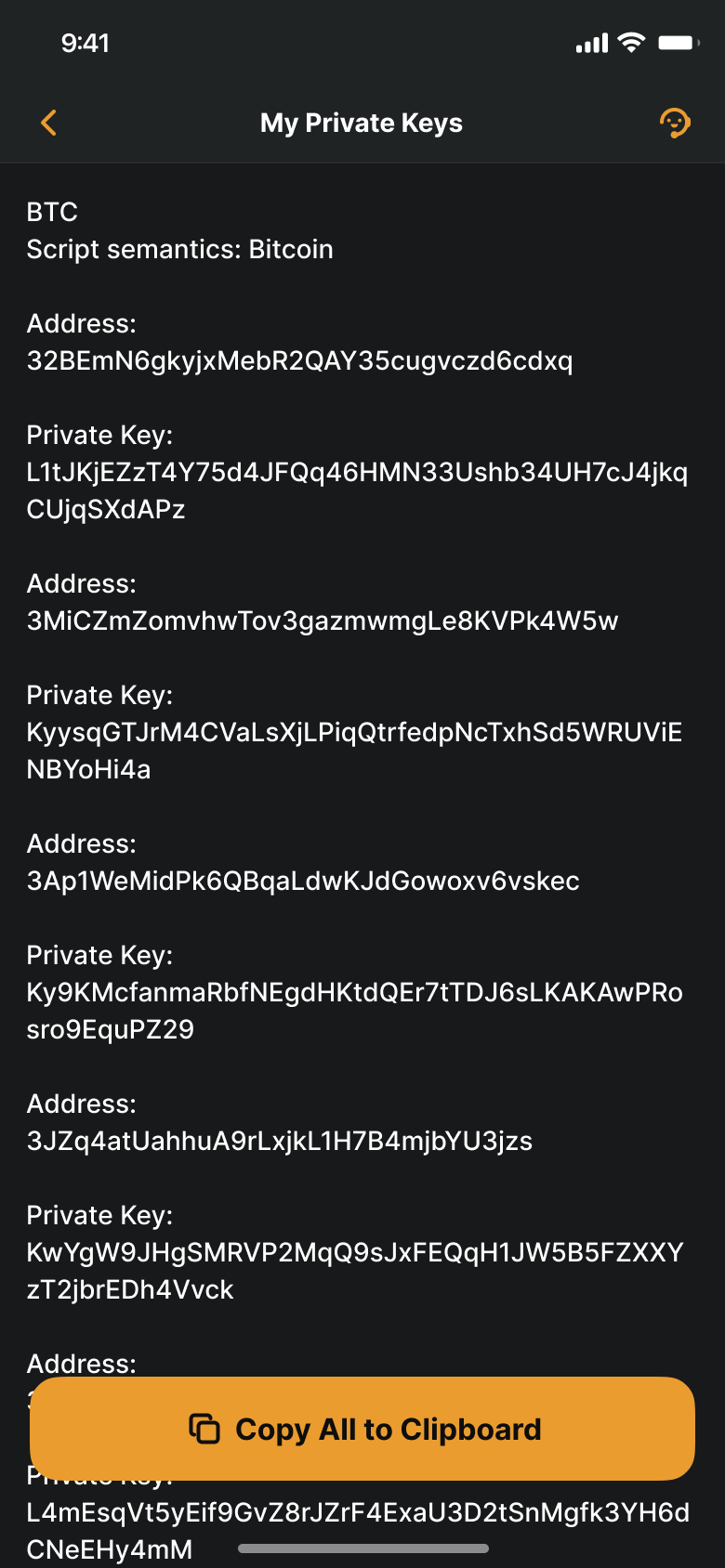
-
- Finally, we were able to load those keys to another wallet and spend the money.
You can check out the transaction on the Bitcoin blockchain: https://www.blockchain.com/btc/address/3MiCZmZomvhwTov3gazmwmgLe8KVPk4W5w
The above would work simultaneously for every single Zengo customer with a valid account, no matter the amount of funds they own.
Conclusions
It is critical to Zengo’s own mission to be able to guarantee customers access to their funds no matter what. Because of the unique approach we have taken with our security design and the role of both the client and the server, we had to create recovery solutions for both sides that are highly reliable, secure, and verifiable –before we have even launched.
To make sure that your funds are safe even if one of the shares is lost, we created innovative backup solutions for all scenarios. We plan to keep investing in this area as we grow.
We have more ideas on how to improve this area. But as of today, our system guarantees you peace of mind.
Last Updated: May 2023
