Prevent damages from Injection Attacks with Software Correction Technology
Wed, Nov 6, 2024-
Tags
Prevent damages from Injection Attacks with Software Correction Technology
Allows developers without expertise to easily correct string manipulation errors during software development
News Highlights:
- We have developed a technology to correct errors in string manipulation, which is a major cause of injection attacks, a serious threat among software vulnerabilities.
- This technology allows software developers without expertise to correct string manipulation errors caused by regular expressions during development.
- Correcting software errors in the operational stage of the service is costly, but this achievement is expected to reduce costs and realize a secure service by correcting errors in the development stage.
TOKYO—October 28, 2024—NTT Corporation (Headquarters: Chiyoda-ku, Tokyo; Representative Member of the Board and President: Akira Shimada; hereinafter “NTT”) and Waseda University (Headquarters: Shinjuku-ku, Tokyo; President: Aiji Tanaka) have developed the world’s first technology to correct errors (bugs) in string operations using string functions in software programs in order to prevent damage from injection attacks, which can lead to information leakage and service suspension.
Injection attacks, one of the greatest threats to exploit software vulnerabilities, are caused primarily by incorrect string manipulation in programs. This technology makes it possible for software developers without specialized knowledge to easily correct errors in string operations in the development stage. Correcting software errors in the operational stage of a service is costly, but since errors can be corrected in the development stage, costs can be reduced and secure services can be realized.
Details of this technology will be announced on October 30, 2024, at the IEEE/ACM ASE 20241, the most premier international conference in the software engineering field, to be held in Sacramento, California.
Background
Attacks that exploit software vulnerabilities are a serious threat in modern society. One of the biggest threats is injection attacks. An injection attack is a method of attacking servers, in which invalid input information is sent to the database used by the server, causing unexpected behavior. The flaw that causes this attack is called an injection vulnerability, and the main cause is a string manipulation error (bug) in a program.
String functions are used to describe string operations in programs that compose software. String functions are provided in many programming languages and are frequently used to describe string operations such as string extraction and replacement searches.
However, when a string function is used to perform a string operation, specialized knowledge about the regular expression2 used by the string function, other input information, and the specification of the string function is required, and it is difficult to describe appropriately.
Programs involving string manipulation are widely used in a variety of software to realize many services, such as processing information entered by a user through a web browser into a form on a website. Errors in string operations can cause the service to malfunction, resulting in information leakage or service shutdown. Cyberattacks that intentionally cause such malfunctions have also appeared, posing a risk to the realization of secure services.
Results of the research
NTT and Waseda University have been jointly researching technologies to automatically correct vulnerabilities and errors that can occur when strings are used in programs. Still, the research has been limited to regular expressions3, 4.
In this achievement, we realized the world’s first technology to correct errors in string operations using string functions in a program based on input/output examples provided by software developers, making it possible to expand the scope of correction to string operations including regular expressions.
Roles
NTT: Formalize the problem and devise corrective measures.
Prof. Tachio Terauchi, Faculty of Science and Engineering, Waseda University: Verify the theoretical accuracy of the method devised by NTT.
Key points of this technology
This technology corrects errors in string operations in programs, which are the main cause of injection attacks, based on input/output examples given by software developers, and ensures that the corrected results are correct.
The key points of this technology are as follows (Figure 1).
① Devised a way to express expected input/output examples of string functions
This allows software developers to express the input and output examples they expect from string functions, including not only the input and output, but also what parts of the input they want to convert and how they want to convert it, rather than using conventional examples that show only the input and output, thus contributing to the output of appropriate correction results. This notation is given using the “Programming by Examples (PBE) 5” method, which generates a program based on examples of input and output that the program must satisfy.
② Strictly defining the behavior of string functions as a theoretical model
Using this definition, it is possible to deduce the conditions under which all input and output examples are satisfied by a parameter that is the information given to the string function to be modified. This technology strictly defines the behavior of string functions conforming to ECMAScript 20236, which is widely used in web applications. This ensures that the modified result satisfies all input and output examples.
③ Based on the theoretical model, we devised a technique to modify the parameters of string functions to satisfy all the examples.
We devised a method for exhaustively searching candidates that can be parameters of the correction result, excluding those that clearly do not satisfy the input/output examples. This approach allows you to complete the correction process in a realistic amount of time. In addition, the modification results can be modified with minimal changes to the parameters before modification, and the software developers can visually check the modification results easily.
This technology makes it possible to correct errors in string operations, which are the main cause of injection attacks, in the development stage, and is expected to contribute to reducing the correction cost and improving the quality of software development.
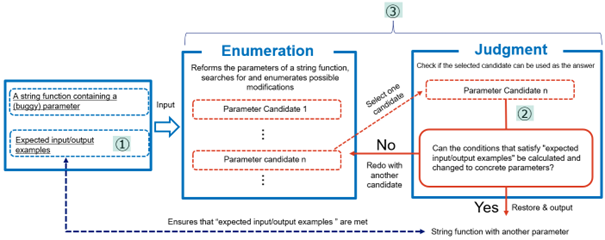
Figure 1 Example of Processing for String Functions
Outlook
Correcting software errors in the service operation stage is costly, but by using this technology, errors can be corrected in the software development stage, which can be expected to reduce costs and realize secure services. There is also a new problem in the automatic generation of programs using AI: how to deal with errors in programs written by unskilled people using AI. This technology, which corrects errors in string operations, is expected to contribute to improving program security without compromising the benefits of AI automation. In the future, we plan to advance research on technology to fix the vulnerability associated with string manipulation.
- ASE (Automated Software Engineering) is the premier international conference in the field of software engineering managed by IEEE/ACM. This technology will be presented at IEEE/ACM ASE 2024 (39th IEEE/ACM International Conference on Automated Software Engineering) from October 27 to November 1, 2024, with the following title and author.
Title: Repairing Regex-Dependent String Functions
Authors: Nariyoshi Chida (NTT Social Informatics Laboratories), Tachio Terauchi (Waseda University)
URL: https://doi.org/10.1145/3691620.3695005 - Regular expression
A simplified rule-based representation of a specific sequence of characters (strings) in a computer, used to search, extract, or replace patterns in a specific string. - NTT and Waseda University develop novel technology for automatically repairing vulnerability of pattern matching function
https://group.ntt/en/newsrelease/2022/03/23/220323b.html - NTT and Waseda University develop novel technology for automatically repairing regular expression error of the extraction function
https://group.ntt/en/newsrelease/2023/06/16/230616b.html - ECMAScript 2023
ECMAScript is a standard for JavaScript, a programming language widely used in Web applications. This technology was verified using ECMAScript revised in 2023. - Programming by Example (PBE)
A method for enabling end users without programming knowledge to create programs. When an example of input/output to be satisfied by a program is given, the technology automatically creates a program to realize it.