An estimated one in every 10 American adults lost money in a cyber scam in the past 12 months, according to a report released by the FTC earlier in the month. On average, each scam victim lost $430, totaling about $9.5 billion overall.
To put this in perspective, that’s over 22 million Americans scammed for $26 million a day, more than $1 million an hour, $18,000 per second.
No one is immune, and now more than ever there is a need to be vigilant. Being taken by a scam can ruin lives or damage the reputation of legitimate companies. No one is excluded—not Amazon, Dell, Malwarebytes, or you.
In the example below, we’ll show how scammers Blue Eye Ventures, LCC, tried to imitate Malwarebytes in order to trick people out of money. Now, more than ever, it’s important to be vigilant in order to tell the good guys from the bad.
Malwarebytes helpline scam
Using a modern web design aesthetic, Blue Eye Ventures makes a reasonably good impression of a company looking to help its clients. They advertise that they are a Malwarebytes helpline. But they are not.
In order to catch these guys in the act, I called the toll-free number asking for help, telling them I wasn’t sure my Malwarebytes software was working properly. I allowed the technician to have access to my computer. He opened up my Malwarebytes software.
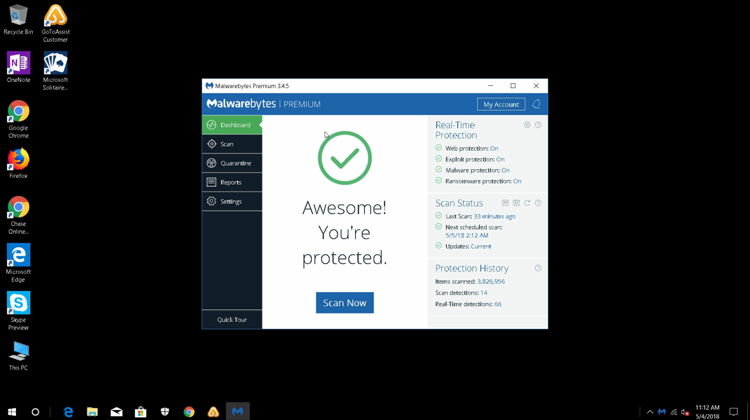
I’m sorry sir, this is fake software
The technician on the phone advised me that the (legitimate) Malwarebytes software I was running was fake. Now, I knew that it was not fake. I ran it minutes earlier and it worked perfectly.Next thing I knew, he ran a tree command. Tree is a recursive directory listing program that produces a depth-indented listing of files. This is not a diagnose tool.
These are the results he produced:
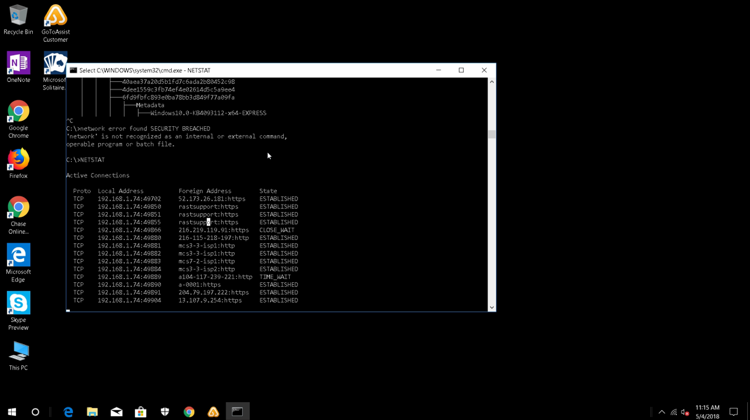
At the bottom of the tree command, he typed “Security Breach” to scare me into believing that my computer was being hacked.
More scare tactics
He then checked my System Configuration:
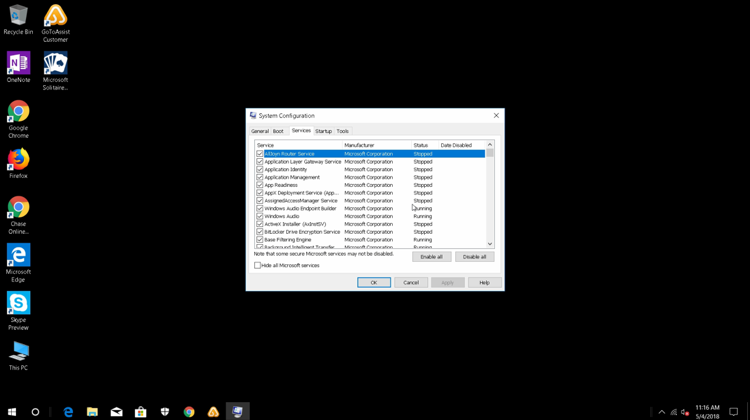
The tech told me that all my software wasn’t running. “It’s stopped.” This was to scare me into believing that my system wasn’t working. Again, he wasn’t using any tools to diagnose hacking or infections.
He then pulled up Resource Monitor:
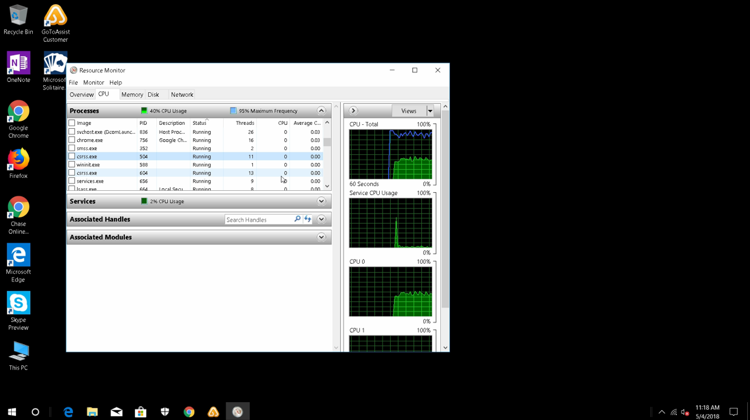
The tech asked me, “Do you know what crss.exe means?” I told him I don’t, even though I do.
The csrss.exe file located in C:WindowsSystem32 is a real file, and removing it will cause problems with your PC. If someone tells you it’s a virus, that’s a hoax.
Case in point, to further scare me into believing my computer was infected, the tech asked me to read the description he pulled up on Google about the csrss.exe file being a Trojan horse or virus.
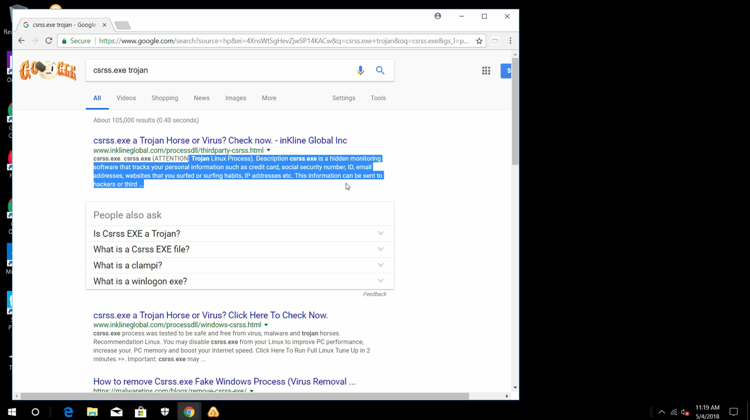
The Google result pulls information from an unreliable and untrustworthy source. For example, the article linked here recommends users remove this “malware” from their Mac systems. Any file with .exe is a Windows executable.
Meanwhile, the scammer still hadn’t checked my system with any real tools to find problems. He was only there to scare me into purchasing his plans.
Do not purchase
Below are the plans he offered me, from one year of support for $200 to a lifetime plan for $700. I was instructed to pay Blue Eye Ventures, LLC, by check. Or I could use my credit card at Easy-installatio.com (phone number +120-3354649). This is a Canadian number—and Malwarebytes’ HQ is in the United States.
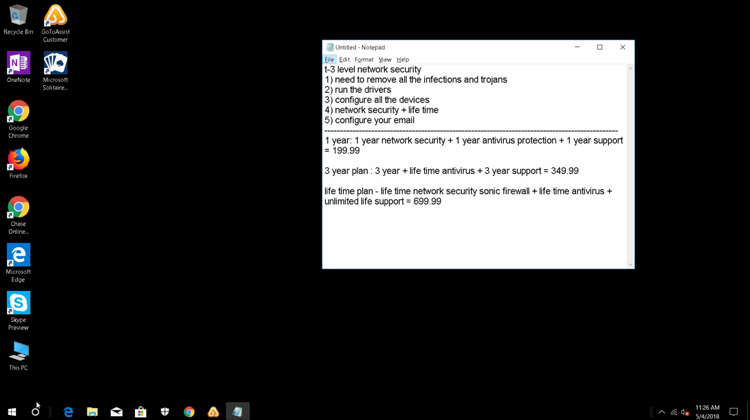
How do you think a real customer would feel? They purchased Malwarebytes and now they are being told that they purchased phony software, their computer is infected, and it’s going cost them hundreds of dollars to repair. Scammers are not only ruining the reputation of legitimate companies, but they are ripping customers off in the process.
At Malwarebytes, we are always working to expose fraud and educate consumers. We will never sell phony software. We will never charge you hundreds of dollars to fix your computer. And we will teach you how to spot the companies who do.










