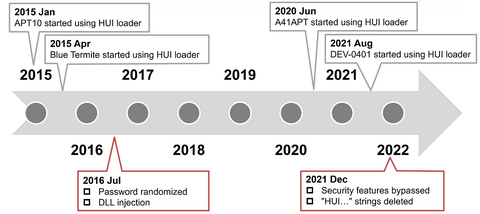
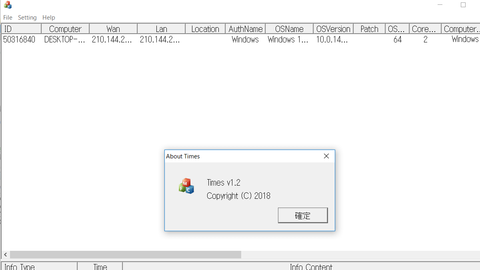
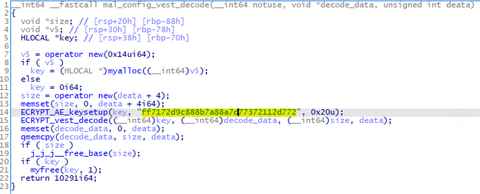
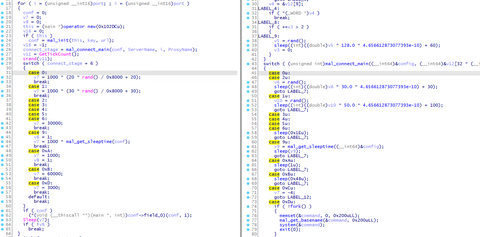
To conceal malware’s features, attackers sometimes encode the malware and decode it only when they execute it. In such cases, the encoded malware is loaded and executed by a program called loader. In this way, an attacker can split the malware into a loader and encoded malware. Minimizing the loader’s features and hiding important features of the malware make detection on infected hosts more difficult. Among such loaders, this article...
List of “朝長 秀誠 (Shusei Tomonaga)”
-
-
Malware targeting Windows OS (PE format) has a variety of obfuscation and packing techniques in place so that they complicate the code analysis processes. On the other hand, there are only a few types of packing techniques for Linux-targeting malware (ELF format), and it is mainly UPX-based. This blog article explains the details of Anti-UPX Unpacking technique, which is often applied to Linux-targeting malware. Malware with Anti-UPX Unpacking Technique The...
-
An attack group BlackTech has been actively conducting attacks against Japanese organisations since 2018. Although it is not as prominent as before, JPCERT/CC is still seeing some cases as of now. This article introduces the details of the malware Gh0stTimes, which is used by this group. Gh0stTimes overview Gh0stTimes is customised based on Gh0st RAT and has been used in some attack cases since 2020. Figure 1 shows the comparison...
-
Volatility 3 had long been a beta version, but finally its v.1.0.0 was released in February 2021. Since Volatility 2 is no longer supported [1], analysts who used Volatility 2 for memory image forensics should be using Volatility 3 already. In this blog post, I introduce a tip for Volatility 3: how to use Volatility 3 offline. This instruction focuses on analyzing Windows OS memory image. What is the problem...
-
The attack group Lazarus (also known as Hidden Cobra) conducts various attack operations. This article introduces malware (VSingle and ValeforBeta) and tools used in attacks against Japanese organisations. VSingle overview VSingle is a HTTP bot which executes arbitrary code from a remote network. It also downloads and executes plugins. Once launched, this malware runs Explorer and executes its main code through DLL injection. (Some samples do not perform DLL injection.)...
-
Lazarus (also known as Hidden Cobra) is known to use various kinds of malware in its attack operations, and we have introduced some of them in our past articles. In this article, we present two more; Torisma and LCPDot. Torisma overview Torisma downloads and executes modules from external servers, and its infection spreads via malicious Word files [1]. Torisma samples that JPCERT/CC has analysed are DLL files and executed as...
-
It is widely known that attackers use Windows commands and tools that are commonly known and used after intruding their target network. Lazarus attack group, a.k.a. Hidden Cobra, also uses such tools to collect information and spread the infection. This blog post describes the tools they use. Lateral movement These three tools are used for lateral movement. AdFind collects the information of clients and users from Active Directory. It has...
-
In a past article, we introduced Linux malware ELF_TSCookie, which is used by an attack group BlackTech. This group also uses other kinds of malware that affects Linux OS. PLEAD module for Windows which we introduced before has its Linux version (ELF_PLEAD) as well. This article describe the details of ELF_PLEAD in comparison to PLEAD module. Comparison between PLEAD Module and ELF_PLEAD ELF_PLEAD and PLEAD module share many parts of...
-
JPCERT/CC has released LogonTracer v1.5, the latest version of the event log analysis tool. While this tool was initially focused on post-incident investigation, we have received many requests for updates for the purpose of real-time log analysis. This time, we made some updates to enable such functions. This article will introduce the details of the update. Further information can be found at the following page: https://github.com/JPCERTCC/LogonTracer/releases/tag/v1.5.0 Support for Elasticsearch LogonTracer...
-
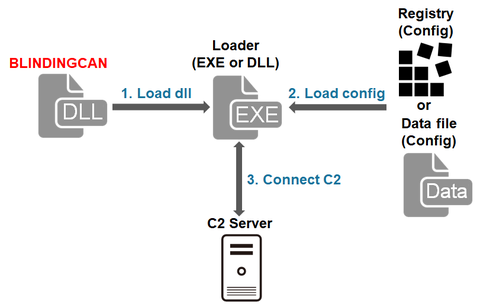
In the previous article, we introduced one type of malware that Lazarus (also known as Hidden Cobra) uses after network intrusion. It is confirmed that this attack group uses multiple types of malware including BLINDINGCAN, which CISA recently introduced in its report [1]. This article summarises the result of our analysis on BLINDINGCAN. BLINDINGCAN overview The malware runs when a loader loads a DLL file. Figure 1 shows the flow...