Heap buffer overflow in WebRTC in Google Chrome prior to 120.0.6099.129 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page.
CVE ID: CVE-2023-7024
Published: 21-Dec-2023, updated 3-Jan-2024
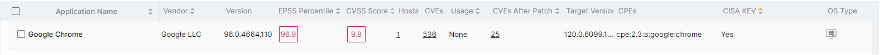
Vulnerable Software: Google Chrome versions below 120.0.6099.129
Severity: High
Potential Impact: High as it allows users to take control of the system
Exploited in the wild: Yes, due to notification published by Google and CISA
Reference:
- CVE listing: https://nvd.nist.gov/vuln/detail/CVE-2023-7024
- CISA KEV (Known Exploited Vulnerability) listing:
https://www.cisa.gov/news-events/alerts/2024/01/02/cisa-adds-two-known-exploited-vulnerabilities-catalog - Google Security Bulletin:
https://chromereleases.googleblog.com/2023/12/stable-channel-update-for-desktop_20.html

Description:
WebRTC (Web Real-Time Communications) provides additional communication functionality to web browsers.
WebRTC is a free, open-source project that allows web browsers and mobile applications to add real-time audio and video peer-to-peer connections and communication functionality allowing quick communication in real time.
You can communicate directly inside web pages and applications without requiring additional plug-ins with these WebRTC data channels. The technology is implemented via regular JavaScript APIs (Application Programming Interfaces) in major web browsers, like Google Chrome, Mozilla Firefox, and Microsoft Edge. For example, a website using this technology can access a user's microphone or webcam. In advanced cases, web apps provide video calling and screen sharing functionality, like in Google Hangouts and similar programs.
Details on how the vulnerability is exploited in the wild have not been published, yet based on the available details end user interaction is required for exploitation of this vulnerability.
The attacker would need to create a crafted HTML page which on clicking would lead to the exploitation of the vulnerability allowing attackers to run malicious code remotely.
Morphisec Protection Mechanisms:
Virtual Patching of the application by Automated Moving Target Defense (AMTD)
Visibility of vulnerable versions of Chrome
How Morphisec prevents the attack:
Morphisec’s AMTD Implementation offers Virtual Patching protection for the vulnerability. Morphisec protects the web browsers and by application of AMTD negates the vulnerability itself by constantly re-arranging the attack surface during application load time
This protection is significant as AMTD application offers signatureless protection and is resistant to changing techniques of the attackers.
Morphisec Exposure Management platforms also provides clear visibility of the systems running vulnerable versions of the application and tags the same with the CISA KEV advisory to better prioritize the patching strategy.
Mitigation recommendations:
- Apply browser updates
- Ensure Morphisec protects all devices with chrome browsers
Want to learn more about how Morphisec stops this and other new and emerging threats? Schedule a demo with our team today.





.png?width=571&height=160&name=iso27001-(2).png)