Analysis of Electromagnetic Information Leakage Based on Cryptographic Integrated Circuits
- PMID: 34828206
- PMCID: PMC8625981
- DOI: 10.3390/e23111508
Analysis of Electromagnetic Information Leakage Based on Cryptographic Integrated Circuits
Abstract
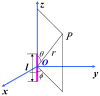
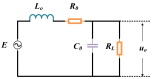
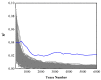
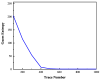
Cryptographic algorithm is the most commonly used method of information security protection for many devices. The secret key of cryptographic algorithm is usually stored in these devices' registers. In this paper, we propose an electromagnetic information leakage model to investigate the relationship between the electromagnetic leakage signal and the secret key. The registers are considered as electric dipole models to illustrate the source of the electromagnetic leakage. The equivalent circuit of the magnetic field probe is developed to bridge the output voltage and the electromagnetic leakage signal. Combining them, the electromagnetic information leakage model's function relationship can be established. Besides, an electromagnetic leakage model based on multiple linear regression is proposed to recover the secret key and the model's effectiveness is evaluated by guess entropy. Near field tests are conducted in an unshielded ordinary indoor environment to investigate the electromagnetic side-channel information leakage. The experiment result shows the correctness of the proposed electromagnetic leakage model and it can be used to recover the secret key of the cryptographic algorithm.
Keywords: electromagnetic leakage; electromagnetic side-channel analysis; guess entropy; integrated circuits; multiple linear regression.
Conflict of interest statement
The authors declare no conflict of interest.
Figures

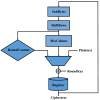
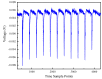
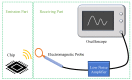
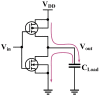
Similar articles
-
A Novel Multi-Objective Electromagnetic Analysis Based on Genetic Algorithm.Sensors (Basel). 2019 Dec 15;19(24):5542. doi: 10.3390/s19245542. Sensors (Basel). 2019. PMID: 31847445 Free PMC article.
-
Tiny Security Hole: First-Order Vulnerability of Masked SEED and Its Countermeasure.Sensors (Basel). 2024 Sep 11;24(18):5894. doi: 10.3390/s24185894. Sensors (Basel). 2024. PMID: 39338639 Free PMC article.
-
Protecting FPGA-Based Cryptohardware Implementations from Fault Attacks Using ADCs.Sensors (Basel). 2024 Feb 29;24(5):1598. doi: 10.3390/s24051598. Sensors (Basel). 2024. PMID: 38475134 Free PMC article.
-
An Optimality Summary: Secret Key Agreement with Physical Unclonable Functions.Entropy (Basel). 2020 Dec 24;23(1):16. doi: 10.3390/e23010016. Entropy (Basel). 2020. PMID: 33374486 Free PMC article. Review.
-
Physical Layer Key Generation in 5G and Beyond Wireless Communications: Challenges and Opportunities.Entropy (Basel). 2019 May 15;21(5):497. doi: 10.3390/e21050497. Entropy (Basel). 2019. PMID: 33267211 Free PMC article. Review.
Cited by
-
Hybrid Threshold Denoising Framework Using Singular Value Decomposition for Side-Channel Analysis Preprocessing.Entropy (Basel). 2023 Jul 28;25(8):1133. doi: 10.3390/e25081133. Entropy (Basel). 2023. PMID: 37628164 Free PMC article.
References
-
- Kocher P.C. Annual International Cryptology Conference. Springer; Berlin/Heidelberg, Germany: 1996. Timing attacks on implementations of Diffie-Hellman, RSA, DSS, and other systems; pp. 104–113.
-
- Xiang Y., Chen Z., Chen Z., Fang Z., Hao H., Chen J., Liu Y., Wu Z., Xuan Q., Yang X. Open dnn box by power side-channel attack. IEEE Trans. Circuits Syst. II Express Briefs. 2020;67:2717–2721. doi: 10.1109/TCSII.2020.2973007. - DOI
-
- Xiang Y., Xu Y., Li Y., Ma W., Xuan Q., Liu Y. Side-channel gray-box attack for dnns. IEEE Trans. Circuits Syst. II Express Briefs. 2020;68:501–505. doi: 10.1109/TCSII.2020.3012005. - DOI
-
- Yang W., Cao Y., Zhou Y., Zhang H., Zhang Q. Distance based leakage alignment for side channel attacks. IEEE Signal Process. Lett. 2016;23:419–423. doi: 10.1109/LSP.2016.2521441. - DOI
-
- Slater D., Novotney S., Moore J., Morgan S., Tenaglia S. Robust keystroke transcription from the acoustic side-channel; Proceedings of the 35th Annual Computer Security Applications Conference; San Juan, PR, USA. 9–13 December 2019; pp. 776–787.
Grants and funding
LinkOut - more resources
Full Text Sources

