Honeyd Research: Disabling Worms With Honeypots
Disabling Worms With Honeypots and Active Immunization
Excerpts from “A Virtual Honeypot Framework”, Niels Provos, 13th USENIX Security Symposium, San Diego, CA, August 2004.
Honeypots are ideally suited to intercept traffic from adversaries that randomly scan the network. This is especially true for Internet worms that use some form of random scanning for new targets, e.g. Blaster or Nimda.
We fight Internet worms using the Honeyd framework and actively counter worm propagation by immunizing infected hosts that contact our virtual honeypots. Analogous to Moore et al., we can model the effect of immunization on worm propagation by using the classic SIR epidemic model. The model states that the number of newly infected hosts increases linearly with the product of infected hosts, fraction of susceptible hosts and contact rate. The immunization is represented by a decrease in new infections that is linear in the number of infected hosts.
The figure below shows a simulated example that tracks the change in the susceptible, infected and immunized populations.
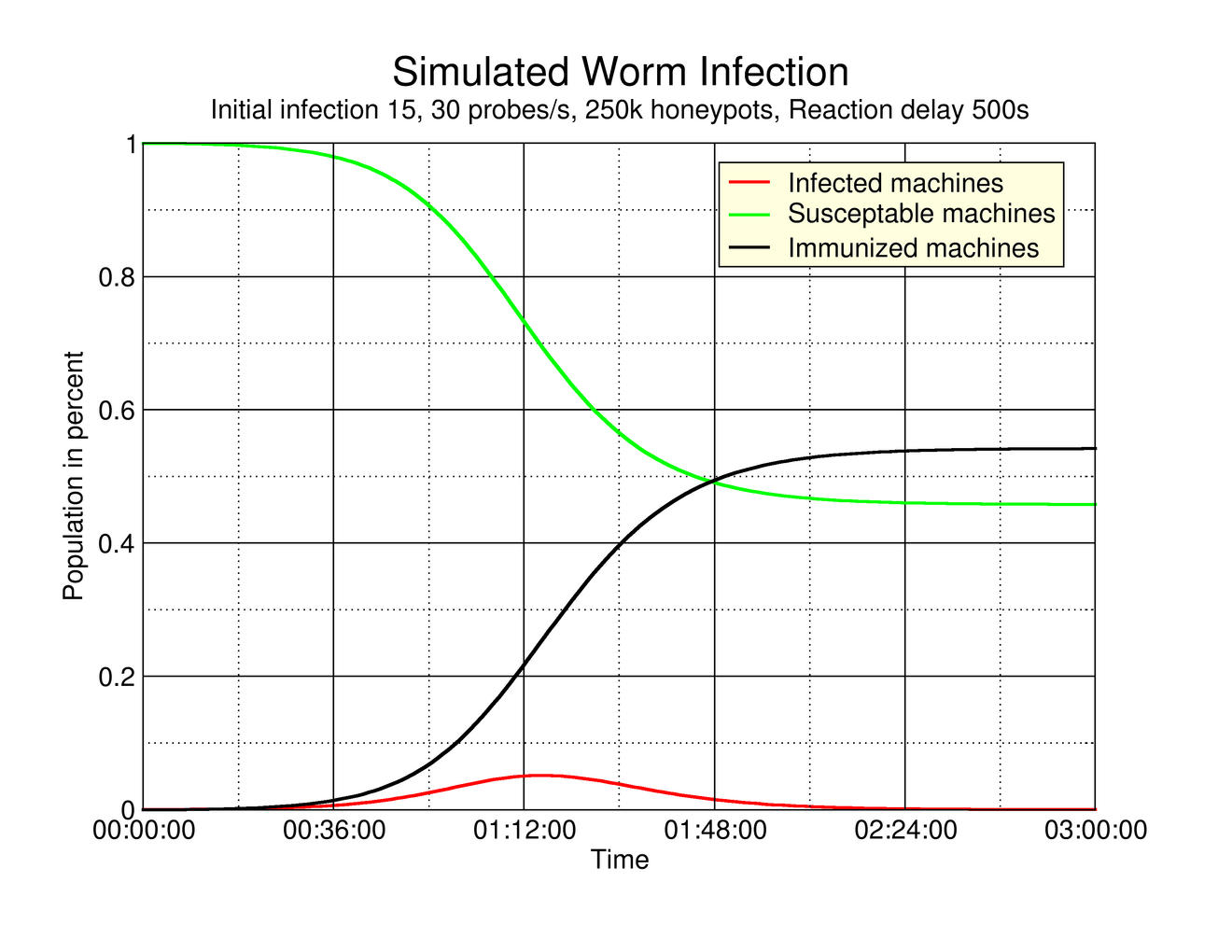
Active Immunization with Virtual Honeypots
Our findings are going to be made available as research paper in the near future. For questions, please contact Niels Provos.
For example, if we assume 360,000 susceptible machines in a 32-bit address space, set the initial worm seed to 150 infected machines and each worm launches 50 probes per second. The simulation measures the effectiveness of using active immunization by virtual honeypots. The honeypots start working after a time delay. The time delay represents the time that is required to detect the worm and install the immunization code. We expect that immunization code can be prepared before a vulnerability is actively exploited. The two figures below show the worm propagation resulting from a varying number of instrumented honeypots. The top graph shows the results if the honeypots are brought online an hour after the worm started spreading.
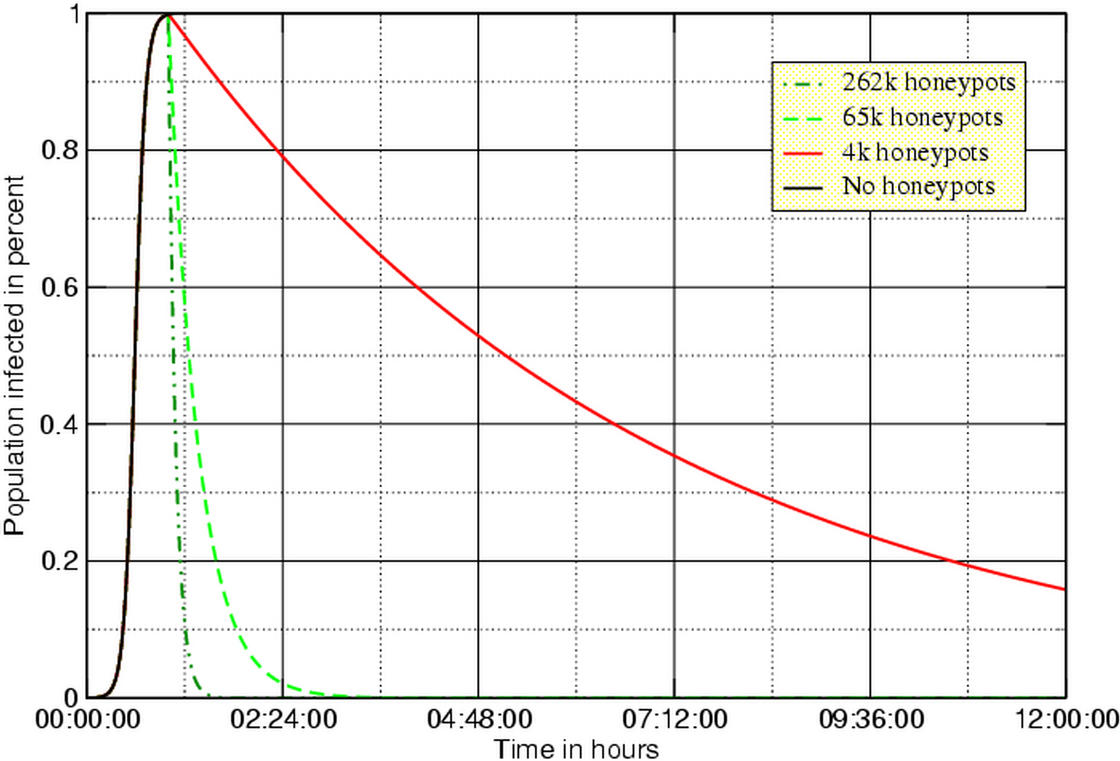
One hour delay time, 50 worm probes per second
The bottom graph shows the results if the honeypots can be activated within 20 minutes.
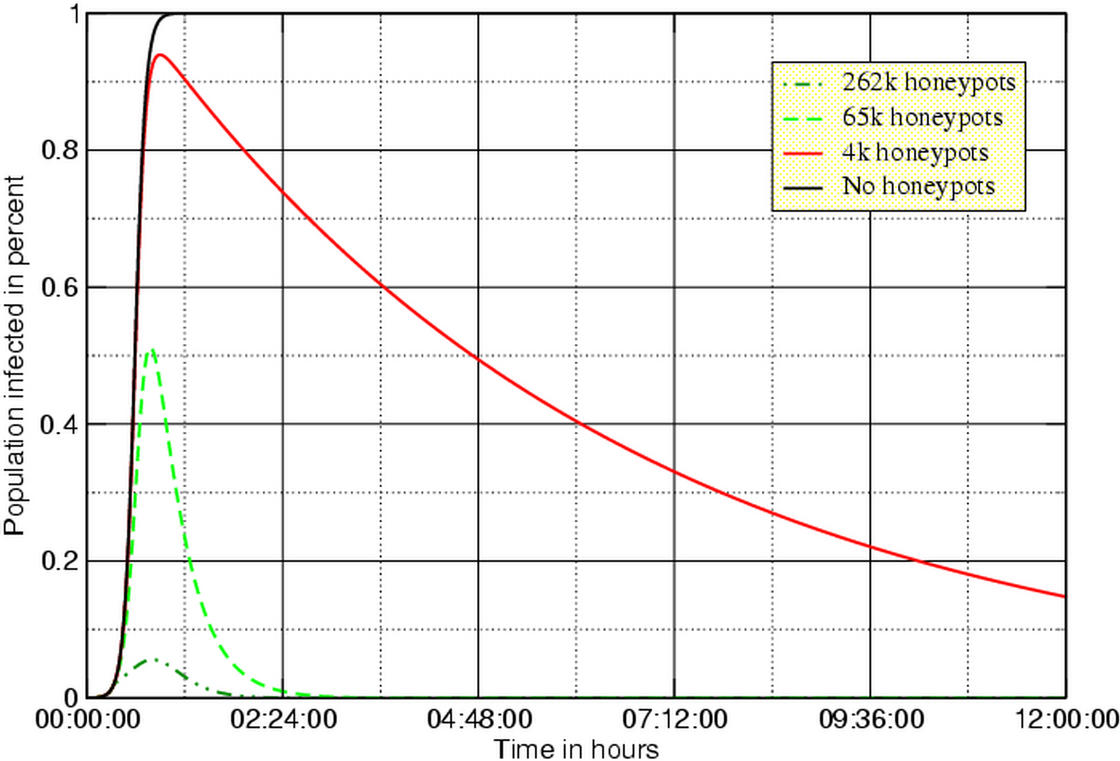
20 minutes delay time, 50 worm probes per second
If we wait for an hour, all vulnerable machines on the Internet will be infected. Our chances are better if we start the honeypots after 20 minutes. In that case, a deployment of about 262,000 honeypots is capable of stopping the worm from spreading.
Alternatively, it would be possible to scan the Internet for vulnerable systems and remotely patch them. For ethical reasons, this is probably unfeasible. However, if we can reliably detect an infected machine with our virtual honeypot framework, then active immunization might be an appropriate response. For the Blaster worm, this idea has been realized by Oudot.
References
Niels Provos, 13th USENIX Security Symposium, San Diego, CA, August 2004.
Internet Quarantine: Requirements for Containing Self-Propagating Code
David Moore, Colleen Shannon, Geoffrey M. Voelker, Stefan Savage, INFOCOM 2003.
Support
If you have suggestions on this research or would like to make resources available, please let me know.